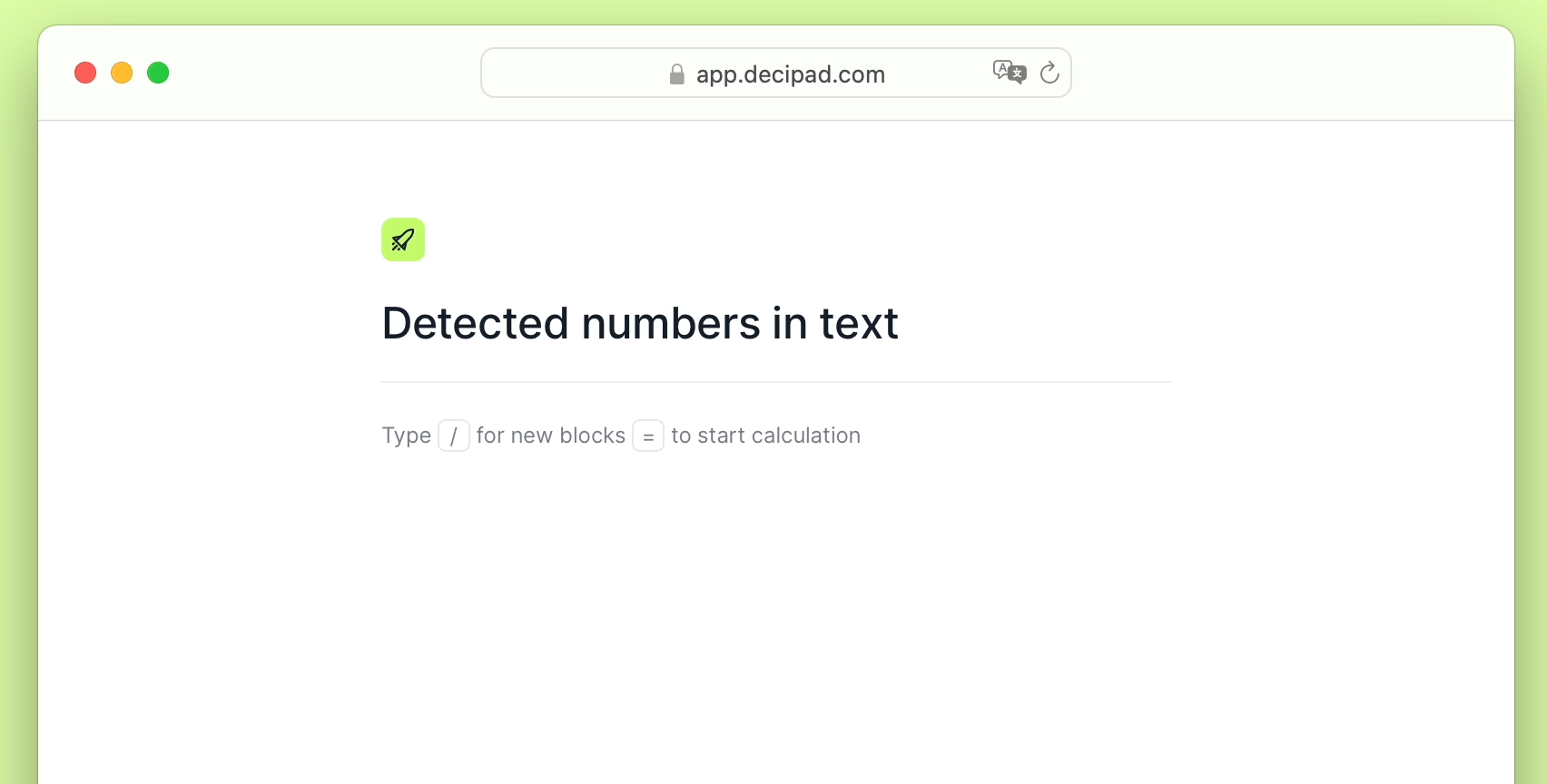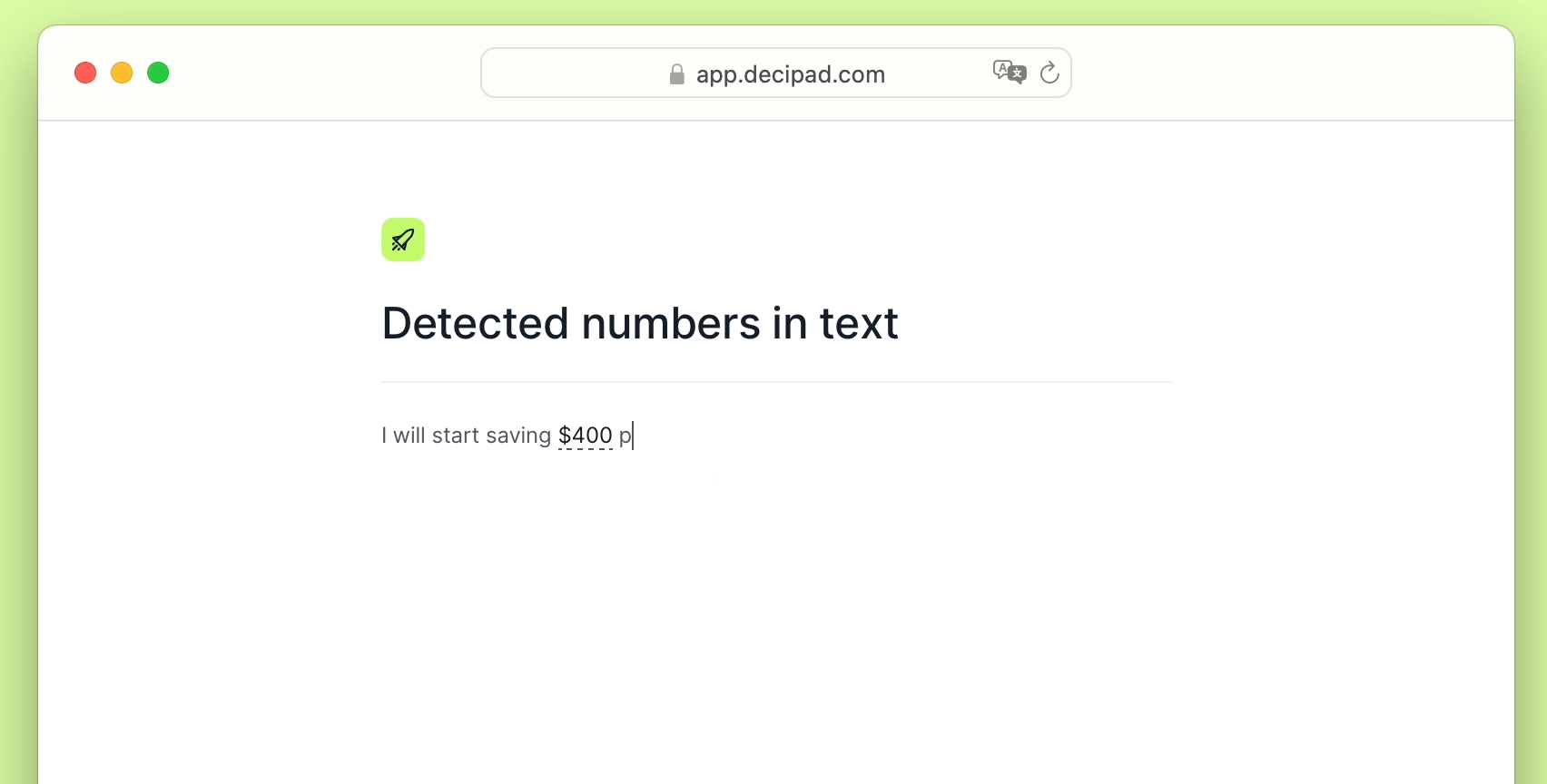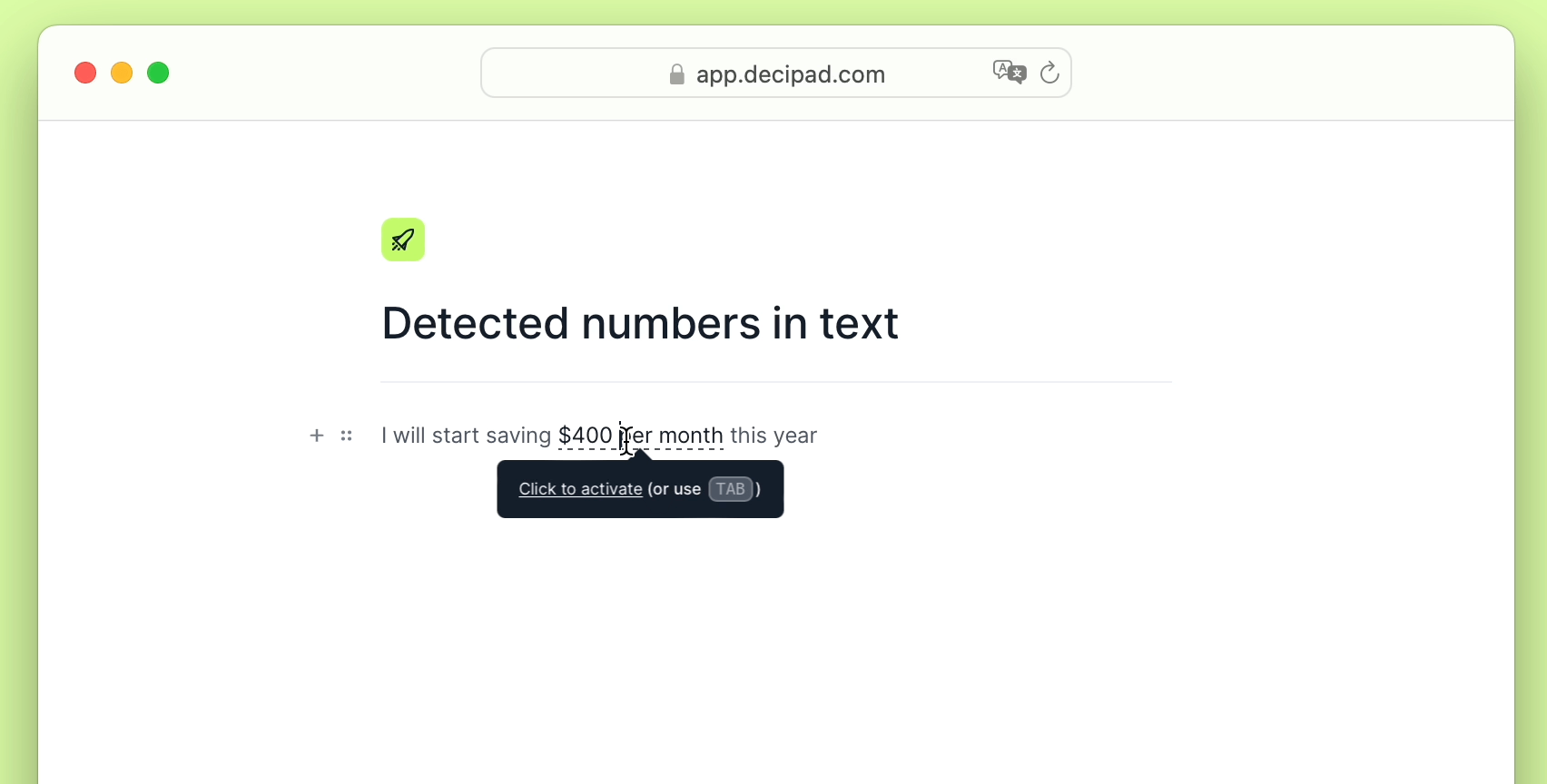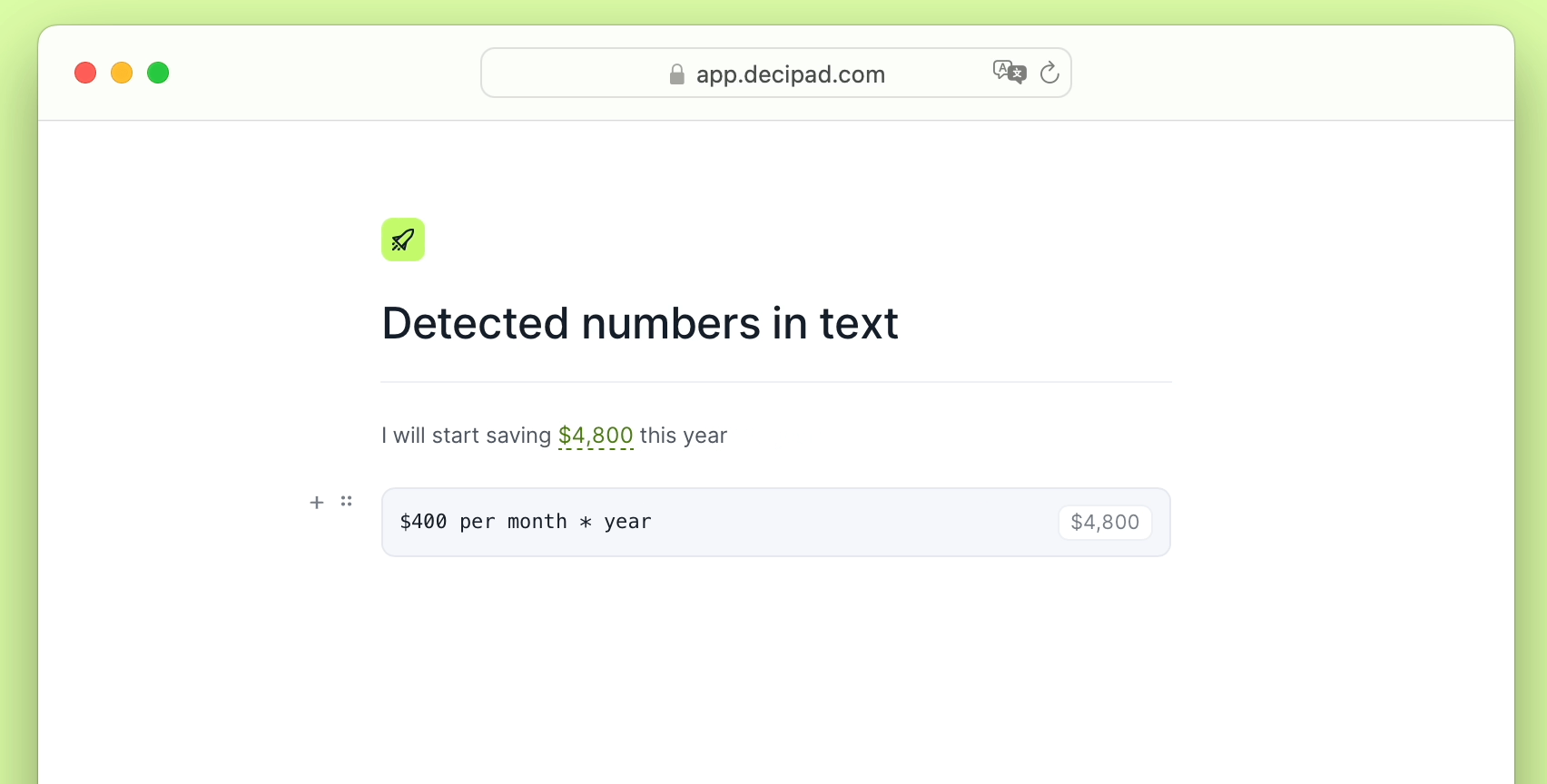
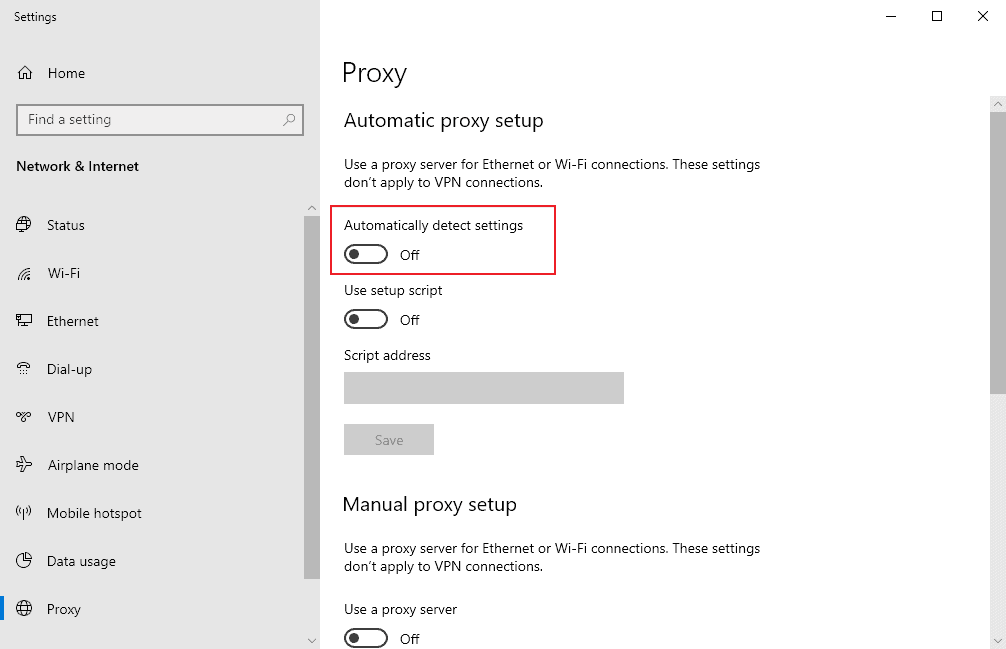
What Everybody Ought To Know About How To Detect Conficker Microsoft

Nessus plugin #36036 performs a network based check for windows computers infected with a variant of the conficker virus.
How to detect conficker microsoft. The scan does not need. Run microsoft's malicious software removal tool. With the office document you want to share open, select share, then copy link from the top on the ribbon.
Microsoft defender antivirus for windows 10 and windows 8.1, or microsoft security. How to detect conficker site microsoft.com. Threats posed by it have only increased with time and we have already deprecated basic authentication across.
Conficker can break into pc. Today we are releasing an open automation framework, pyrit (python risk identification toolkit for generative ai), to empower security professionals and machine. Conficker is programmed to contact its creators over the internet via a number of pseudorandom urls, which change on a daily basis in order to conceal its.
Microsoft defender antivirus for windows 10 and windows 8.1, or microsoft security essentials for windows 7 and windows vista; Use the following free microsoft software to detect and remove this threat: It is well advised that you obtain the.
Also do these to cleanup general corruption and repair/replace damaged/missing system files. The conficker worm got its start in november 2008, when it was discovered by microsoft malware protection center infecting computers via two mechanisms,. The presence of a conficker/downadup infection may be detected if a user is unable to surf to their security solution website or if they are unable to connect to the.
Microsoft security software detects and removes this threat. Download and install wireshark on a computer that is constantly getting dropped on by a. Basic authentication is an outdated industry standard.
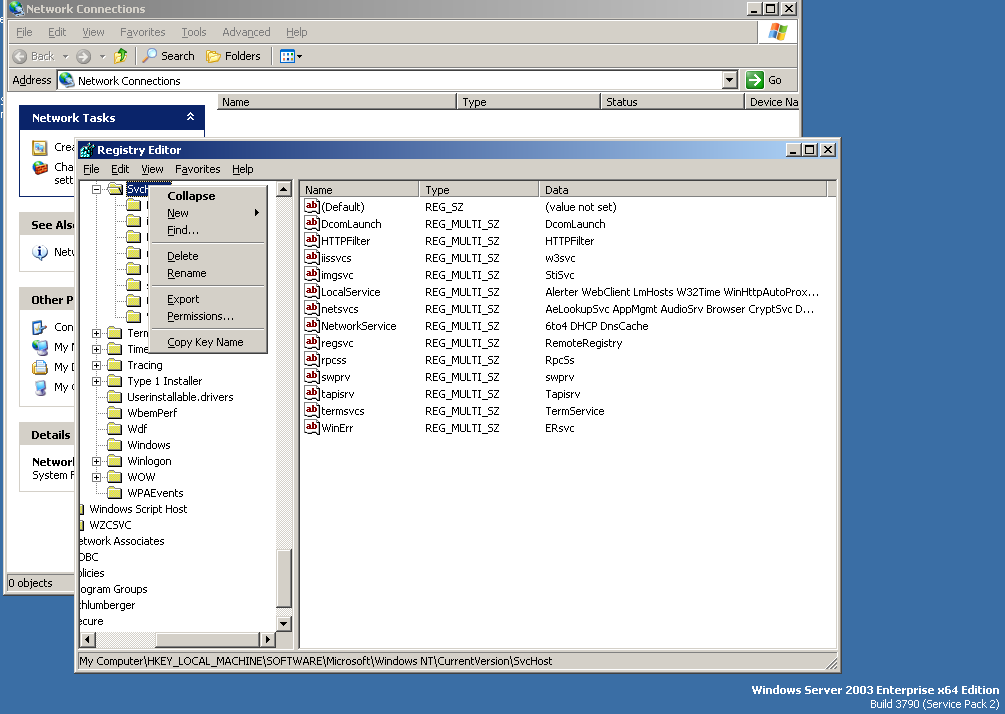
Detecting conficker files and registry; If you installed certain older apple apps for windows, or used boot camp to install windows on mac, you also have apple software update.